PC Lab 5: Diferență între versiuni
Cbira (discuție | contribuții) Fără descriere a modificării |
Cbira (discuție | contribuții) Fără descriere a modificării |
||
| Linia 4: | Linia 4: | ||
'''Task: run an open-source profiler (valgrind & gprof or visual studio) and improve performance of keypoint extraction in ASIFT C++ code''' | '''Task: run an open-source profiler (valgrind & gprof or visual studio) and improve performance of keypoint extraction in ASIFT C++ code''' | ||
1. Download ASIFT project from here: http://www.ipol.im/pub/art/2011/my-asift/ | |||
2. Run demo_ASIFT with the two included Adams as input images from the Sixtine Chapel. Horizontal result should look like this: [[Fișier:Hadam.png]] | |||
3. Modify code to only do "compute_asift_keypoints" (matching is not interesting, since it was covered in the previous session) | |||
4. Run the valgrind profiler | |||
eg, for cpuload program: | eg, for cpuload program: | ||
g++ -std=c++11 cpuload.cpp -o cpuload (compile program cpuload) | g++ -std=c++11 cpuload.cpp -o cpuload (compile program cpuload) | ||
valgrind --tool=callgrind ./cpuload (run the program with callgrind; generates a file callgrind.out.12345 that can be viewed with kcachegrind) | valgrind --tool=callgrind ./cpuload (run the program with callgrind; generates a file callgrind.out.12345 that can be viewed with kcachegrind) | ||
kcachegrind profile.callgrind // open profile.callgrind with kcachegrind | kcachegrind profile.callgrind // open profile.callgrind with kcachegrind | ||
Versiunea de la data 12 aprilie 2018 16:00
Session 5
Task: run an open-source profiler (valgrind & gprof or visual studio) and improve performance of keypoint extraction in ASIFT C++ code
1. Download ASIFT project from here: http://www.ipol.im/pub/art/2011/my-asift/
2. Run demo_ASIFT with the two included Adams as input images from the Sixtine Chapel. Horizontal result should look like this: 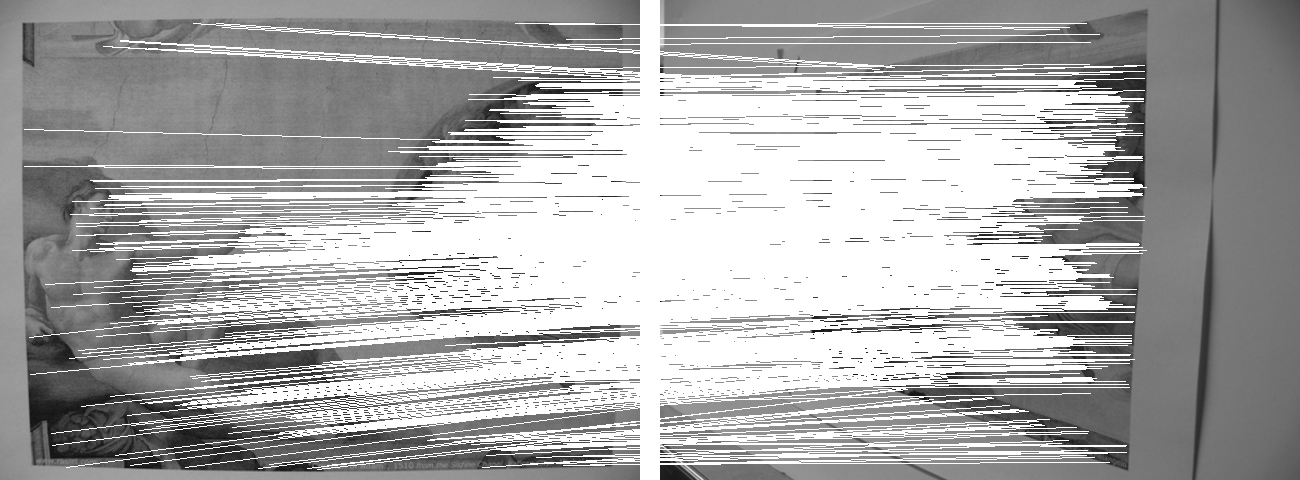 3. Modify code to only do "compute_asift_keypoints" (matching is not interesting, since it was covered in the previous session)
4. Run the valgrind profiler
3. Modify code to only do "compute_asift_keypoints" (matching is not interesting, since it was covered in the previous session)
4. Run the valgrind profiler
eg, for cpuload program:
g++ -std=c++11 cpuload.cpp -o cpuload (compile program cpuload)
valgrind --tool=callgrind ./cpuload (run the program with callgrind; generates a file callgrind.out.12345 that can be viewed with kcachegrind)
kcachegrind profile.callgrind // open profile.callgrind with kcachegrind
Note: Valgrind is also great for checking memory leaks:
valgrind --leak-check=full <path>
valgrind --tool=memcheck <path>
Points (out of 10) vs. expected performance ():
TBD